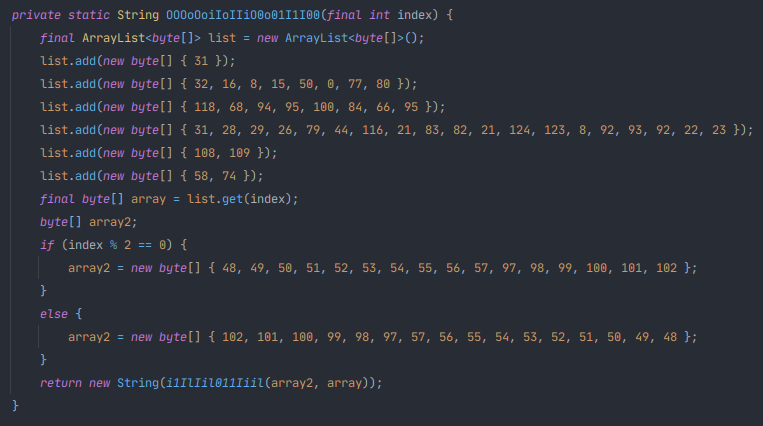
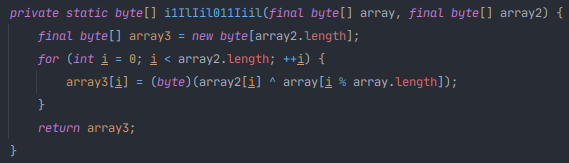
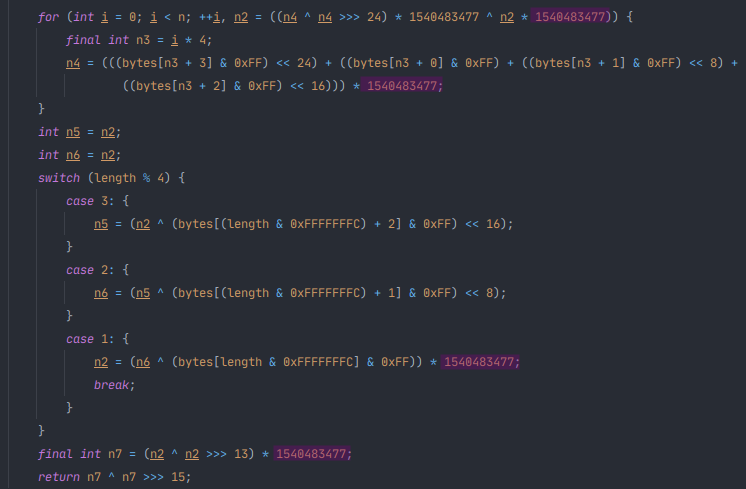
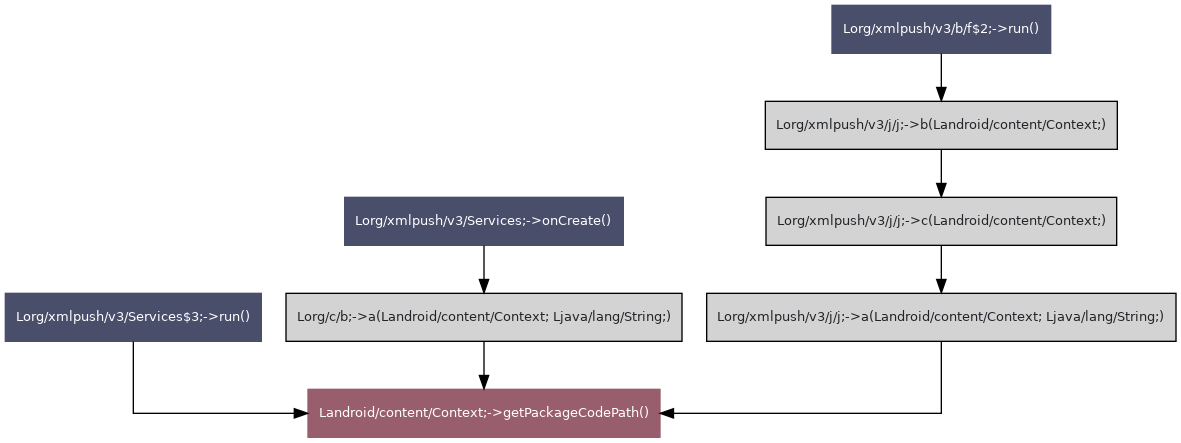
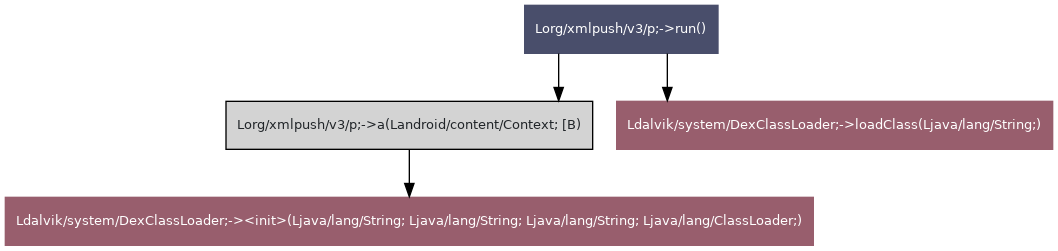
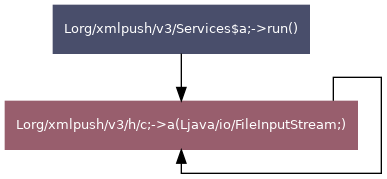
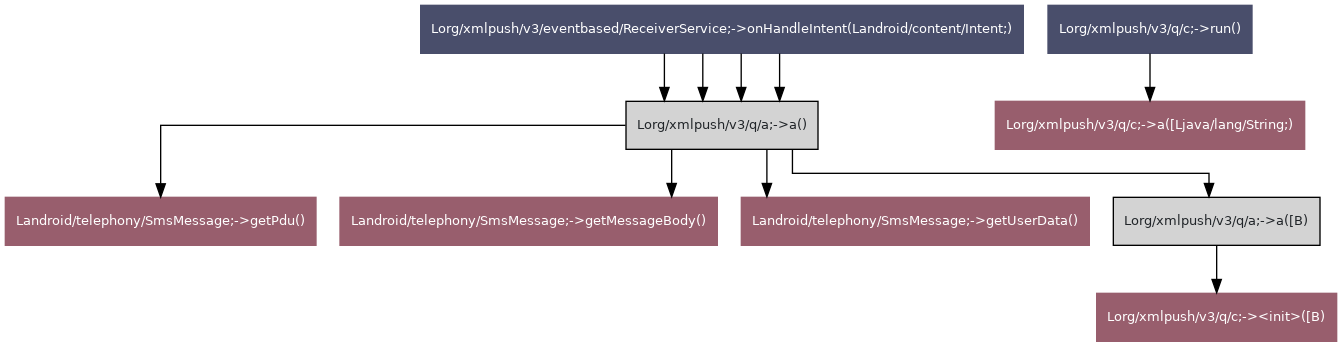
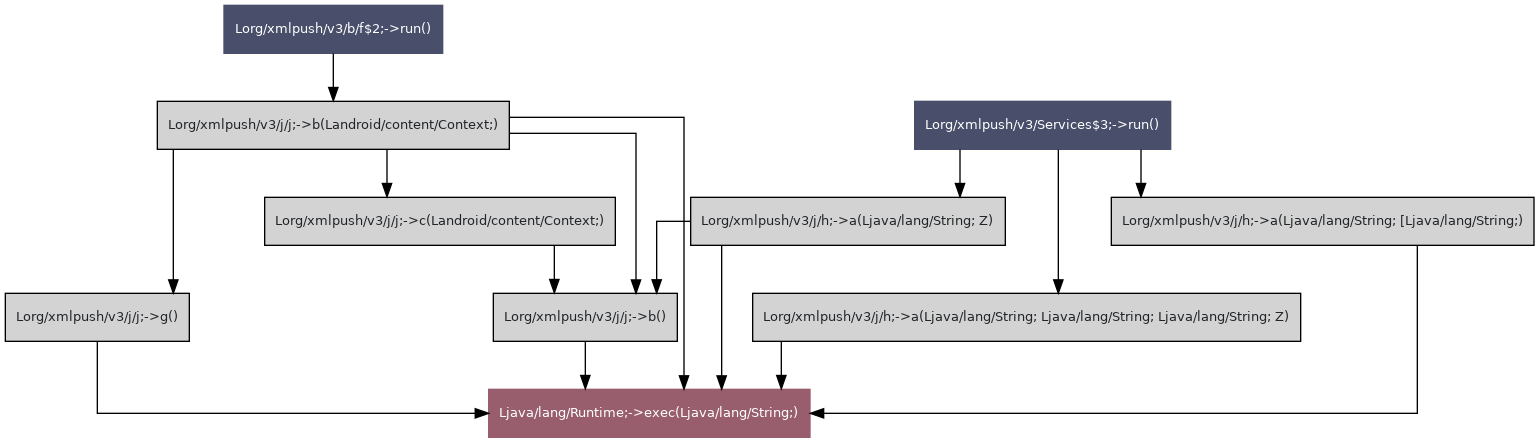
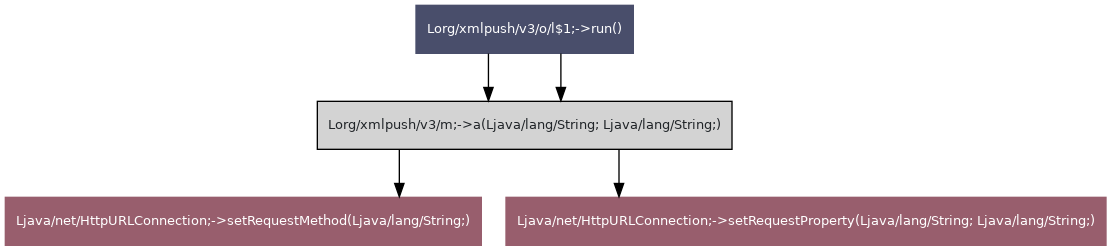
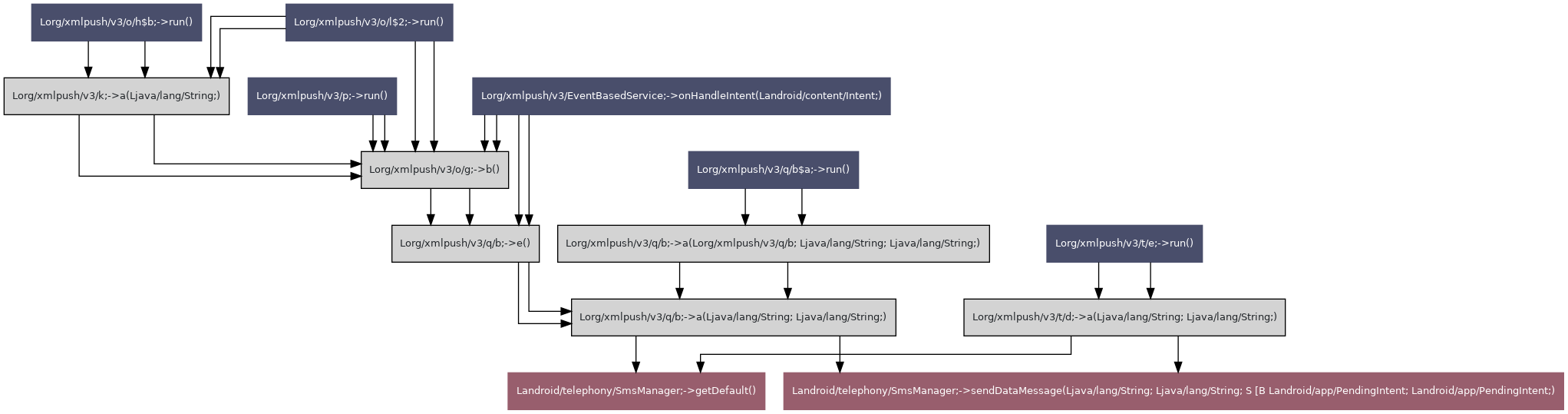
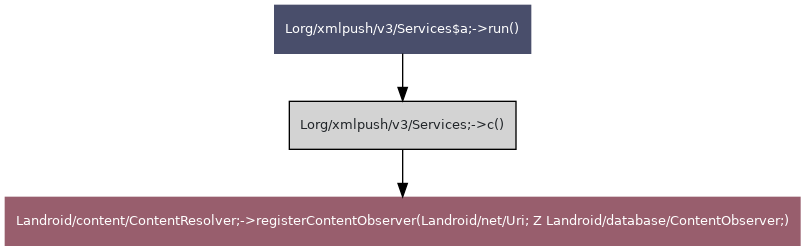
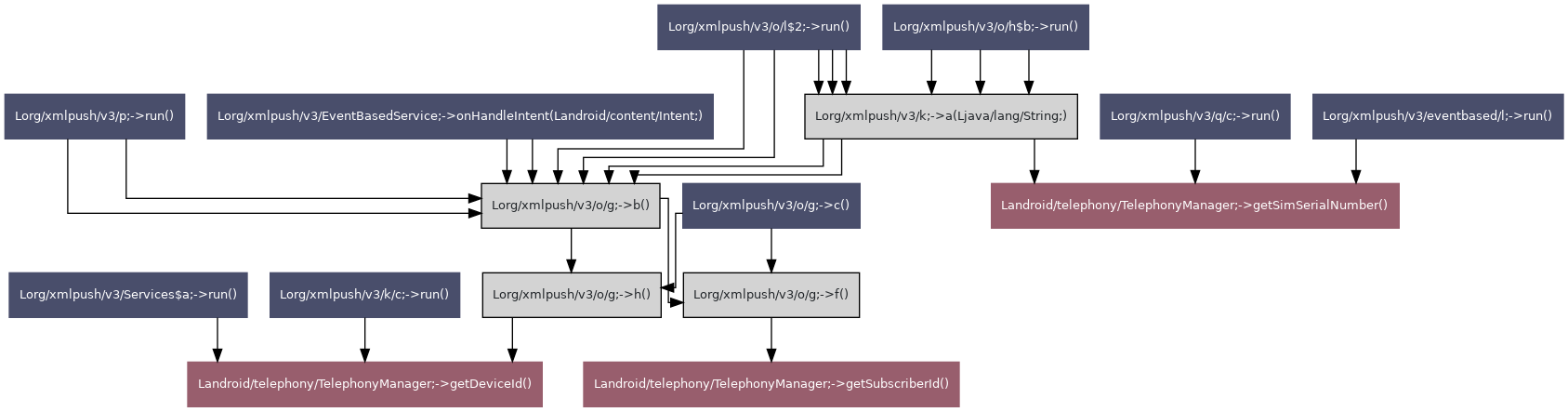
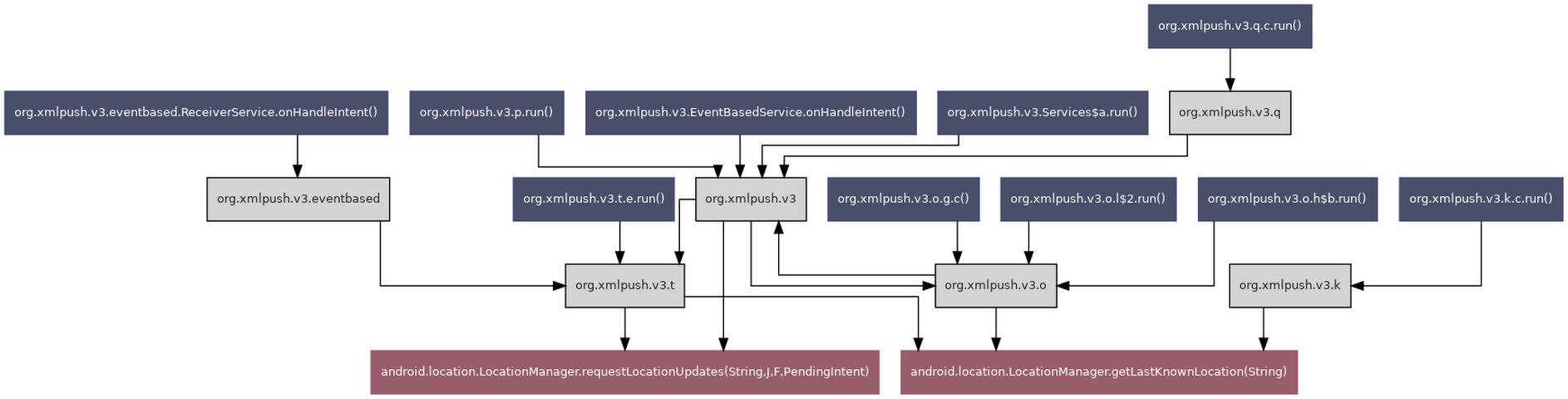
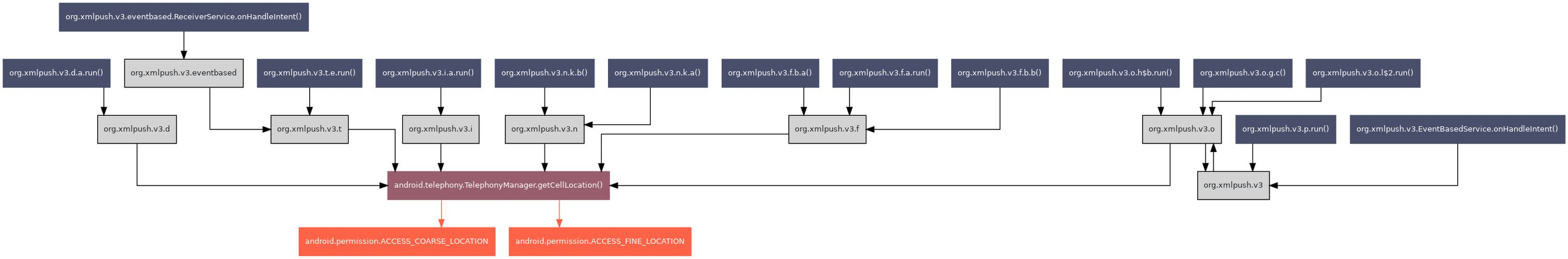
| Group ID | Group name | TLV value | Known TLV | TLV name |
| 64 | drives all get | 131488 | ✔ | TlvTypeGetAllDrivesRequest |
| 64 | drives all get | 131744 | ✔ | TlvTypeGetAllDrivesReply |
| 66 | contents folder get | 135328 | ✔ | TlvTypeGetFolderContentsRequest |
| 66 | contents folder get | 135584 | ✔ | TlvTypeGetFolderContentsReply |
| 66 | contents folder get | 135840 | ✔ | TlvTypeGetFolderContentsNext |
| 66 | contents folder get | 136096 | ✔ | TlvTypeGetFolderContentsEnd |
| 68 | download file | 139424 | ✔ | TlvTypeDownloadFileRequest |
| 68 | download file | 139680 | ✔ | TlvTypeCancelDownloadFileRequest |
| 68 | download file | 139936 | ✔ | TlvTypeDownloadFileReply |
| 68 | download file | 140192 | ✔ | TlvTypeDownloadFileNext |
| 68 | download file | 140448 | ✔ | TlvTypeDownloadFileEnd |
| 68 | download file | 140704 | ✔ | TlvTypeCancelDownloadFileReply |
| 70 | upload file | 143520 | ✔ | TlvTypeUploadFileRequest |
| 70 | upload file | 143776 | ✔ | TlvTypeCancelUploadFileRequest |
| 70 | upload file | 144032 | ✔ | TlvTypeUploadFileReply |
| 70 | upload file | 144288 | ✔ | TlvTypeUploadFileNext |
| 70 | upload file | 144544 | ✔ | TlvTypeUploadFileEnd |
| 70 | upload file | 144800 | ✔ | TlvTypeUploadFileCompleted |
| 70 | upload file | 145056 | ✔ | TlvTypeCancelUploadFileReply |
| 72 | delete file | 147616 | ✔ | TlvTypeDeleteFileRequest |
| 72 | delete file | 147872 | ✔ | TlvTypeDeleteFileReply |
| 74 | search file | 151968 | ✔ | TlvTypeSearchFileRequest |
| 74 | search file | 152224 | ✔ | TlvTypeSearchFileReply |
| 74 | search file | 152480 | ✔ | TlvTypeSearchFileNext |
| 74 | search file | 152736 | ✔ | TlvTypeSearchFileEnd |
| 74 | search file | 152992 | ✔ | TlvTypeCancelSearchFileRequest |
| 74 | search file | 153248 | ✔ | TlvTypeCancelSearchFileReply |
| 78 | fs | 159888 | ✔ | TlvTypeFSFileDataChunk |
| 78 | fs | 160128 | ✔ | TlvTypeFSDiskDrive |
| 78 | fs | 160384 | ✔ | TlvTypeFSFullPath |
| 78 | fs | 160640 | ✔ | TlvTypeFSFilename |
| 78 | fs | 160896 | ✔ | TlvTypeFSFileExtension |
| 78 | fs | 161088 | ✔ | TlvTypeFSDiskDriveType |
| 78 | fs | 161408 | ✔ | TlvTypeFSFileSize |
| 78 | fs | 161584 | ✔ | TlvTypeFSIsFolder |
| 79 | fs | 161840 | ✔ | TlvTypeFSReadOnly |
| 79 | fs | 162096 | ✔ | TlvTypeFSHidden |
| 79 | fs | 162352 | ✔ | TlvTypeFSSystem |
| 79 | fs | 162688 | ✔ | TlvTypeFSFileCreationTime |
| 79 | fs | 162944 | ✔ | TlvTypeFSFileLastAccessTime |
| 79 | fs | 163200 | ✔ | TlvTypeFSFileLastWriteTime |
| 79 | fs | 163472 | ✔ | TlvTypeFSFullPathM |
| 79 | fs | 163632 | × | unknown |
| 82 | system config file | 168096 | ✔ | TlvTypeGetFileSystemConfigRequest |
| 82 | system config file | 168352 | ✔ | TlvTypeFileSystemConfigReply |
| 82 | system config file | 168608 | ✔ | TlvTypeSetFileSystemConfigRequest |
| 128 | line cmd | 262560 | ✔ | TlvTypeStartCmdLineSessionRequest |
| 128 | line cmd | 262816 | ✔ | TlvTypeStartCmdLineSessionReply |
| 128 | line cmd | 263072 | ✔ | TlvTypeStopCmdLineSessionRequest |
| 128 | line cmd | 263328 | ✔ | TlvTypeCmdLineSessionStoppedReply |
| 128 | line cmd | 263584 | ✔ | TlvTypeCmdLineExecute |
| 128 | line cmd | 263840 | ✔ | TlvTypeCmdLineExecutionResult |
| 130 | line cmd execute | 266352 | ✔ | TlvTypeCmdLineExecuteCommand |
| 130 | line cmd execute | 266560 | ✔ | TlvTypeCmdLineExecuteAnswerID |
| 130 | line cmd execute | 266864 | ✔ | TlvTypeCmdLineExecuteAnswerData |
| 146 | line config cmd | 299168 | ✔ | TlvTypeGetCmdLineConfigRequest |
| 146 | line config cmd | 299424 | ✔ | TlvTypeCmdLineConfigReply |
| 146 | line config cmd | 299680 | ✔ | TlvTypeSetCmdLineConfigRequest |
| 160 | config scheduler | 328096 | ✔ | TlvTypeGetSchedulerConfigRequest |
| 160 | config scheduler | 328352 | ✔ | TlvTypeSchedulerConfigReply |
| 160 | config scheduler | 328608 | ✔ | TlvTypeSetSchedulerConfigRequest |
| 162 | task scheduler | 331920 | ✔ | TlvTypeSchedulerTask |
| 162 | task scheduler | 332192 | ✔ | TlvTypeSchedulerTaskRecordByTime |
| 162 | task scheduler | 332448 | ✔ | TlvTypeSchedulerTaskRecordScreenWhenAppRuns |
| 162 | task scheduler | 332704 | ✔ | TlvTypeSchedulerTaskRecordMicWhenAppUsesIt |
| 162 | task scheduler | 332960 | ✔ | TlvTypeSchedulerTaskRecordWebCamWhenAppUsesIt |
| 176 | sch | 360592 | ✔ | TlvTypeSCHTaskConfiguration |
| 176 | sch | 360752 | ✔ | TlvTypeSCHTaskEnabled |
| 176 | sch | 361344 | ✔ | TlvTypeSCHTaskStartDateTime |
| 176 | sch | 361600 | ✔ | TlvTypeSCHTaskStopDateTime |
| 176 | sch | 362112 | ✔ | TlvTypeSCHApplicationName |
| 176 | sch | 362288 | ✔ | TlvTypeSCHApplicationWindowOnly |
| 512 | microphone | 1048992 | ✔ | TlvTypeStartMicrophoneRequest |
| 512 | microphone | 1049248 | ✔ | TlvTypeStartMicrophoneReply |
| 512 | microphone | 1049504 | ✔ | TlvTypeMicrophoneFrame |
| 512 | microphone | 1049760 | ✔ | TlvTypeStopMicrophoneRequest |
| 512 | microphone | 1050016 | ✔ | TlvTypeMicrophoneStoppedReply |
| 512 | microphone | 1050272 | ✔ | TlvTypeStartMicrophoneRecording |
| 514 | | 1052736 | ✔ | TlvTypeMICFrameID |
| 514 | | 1053072 | ✔ | TlvTypeMICFrameData |
| 514 | | 1053312 | ✔ | TlvTypeAudioSessionType |
| 514 | | 1053568 | ✔ | TlvTypeAudioEncodingType |
| 518 | audio config | 1061024 | ✔ | TlvTypeGetAudioConfigRequest |
| 518 | audio config | 1061280 | ✔ | TlvTypeAudioConfigReply |
| 518 | audio config | 1061536 | ✔ | TlvTypeSetAudioConfigRequest |
| 520 | type video | 1066112 | ✔ | TlvTypeVideoSessionType |
| 520 | type video | 1066368 | ✔ | TlvTypeVideoEncodingType |
| 544 | screen | 1114528 | ✔ | TlvTypeStartScreenRequest |
| 544 | screen | 1114784 | ✔ | TlvTypeStartScreenReply |
| 544 | screen | 1115040 | ✔ | TlvTypeScreenFrame |
| 544 | screen | 1115296 | ✔ | TlvTypeStopScreenRequest |
| 544 | screen | 1115552 | ✔ | TlvTypeScreenStoppedReply |
| 544 | screen | 1115808 | ✔ | TlvTypeStartScreenRecording |
| 548 | cam web | 1122720 | ✔ | TlvTypeStartWebCamRequest |
| 548 | cam web | 1122976 | ✔ | TlvTypeStartWebCamReply |
| 548 | cam web | 1123232 | ✔ | TlvTypeWebCamFrame |
| 548 | cam web | 1123488 | ✔ | TlvTypeStopWebCamRequest |
| 548 | cam web | 1123744 | ✔ | TlvTypeWebCamStoppedReply |
| 548 | cam web | 1124000 | ✔ | TlvTypeStartWebCamRecording |
| 550 | config video | 1126560 | ✔ | TlvTypeGetVideoConfigRequest |
| 550 | config video | 1126816 | ✔ | TlvTypeVideoConfigReply |
| 550 | config video | 1127072 | ✔ | TlvTypeSetVideoConfigRequest |
| 552 | | 1130560 | ✔ | TlvTypeVDFrameID |
| 552 | | 1130896 | ✔ | TlvTypeVDFrameData |
| 552 | | 1131136 | ✔ | TlvTypeOriginalVideoResolution |
| 552 | | 1131392 | ✔ | TlvTypeVideoResolution |
| 552 | | 1132160 | ✔ | TlvTypeAutomaticRecordingUID |
| 576 | key logging | 1180064 | ✔ | TlvTypeStartKeyLoggingRequest |
| 576 | key logging | 1180320 | ✔ | TlvTypeStartKeyLoggingReply |
| 576 | key logging | 1180576 | ✔ | TlvTypeKeyLoggingFrame |
| 576 | key logging | 1180832 | ✔ | TlvTypeStopKeyLoggingRequest |
| 576 | key logging | 1181088 | ✔ | TlvTypeKeyLoggingStoppedReply |
| 582 | config keylogger | 1192096 | ✔ | TlvTypeGetKeyloggerConfigRequest |
| 582 | config keylogger | 1192352 | ✔ | TlvTypeKeyloggerConfigReply |
| 582 | config keylogger | 1192608 | ✔ | TlvTypeSetKeyloggerConfigRequest |
| 584 | kl frame data | 1196416 | ✔ | TlvTypeKLFrameData |
| 640 | skype | 1311136 | ✔ | TlvTypeSkypeAudioMetaInfo |
| 640 | skype | 1311376 | ✔ | TlvTypeSkypeAudioRecording |
| 640 | skype | 1311648 | ✔ | TlvTypeSkypeTextRecording |
| 640 | skype | 1311904 | ✔ | TlvTypeSkypeFileMetaInfo |
| 640 | skype | 1312144 | ✔ | TlvTypeSkypeFileRecording |
| 640 | skype | 1312416 | ✔ | TlvTypeSkypeContactsRecording |
| 640 | skype | 1312640 | ✔ | TlvTypeSkypeContactsUserData |
| 646 | config skype | 1323168 | ✔ | TlvTypeGetSkypeConfigRequest |
| 646 | config skype | 1323424 | ✔ | TlvTypeSkypeConfigReply |
| 646 | config skype | 1323680 | ✔ | TlvTypeSetSkypeConfigRequest |
| 646 | config skype | 1324336 | ✔ | TlvTypeConfigSkypeAudioEnable |
| 646 | config skype | 1324592 | ✔ | TlvTypeConfigSkypeTextEnable |
| 646 | config skype | 1324848 | ✔ | TlvTypeConfigSkypeFileEnable |
| 647 | config contacts enable list skype | 1325104 | ✔ | TlvTypeConfigSkypeContactsListEnable |
| 648 | skype | 1327232 | ✔ | TlvTypeSkypeAudioEncodingType |
| 648 | skype | 1327488 | ✔ | TlvTypeSkypeLoggedInUserAccountName |
| 648 | skype | 1327744 | ✔ | TlvTypeSkypeConversationPartnerAccountName |
| 648 | skype | 1328000 | ✔ | TlvTypeSkypeConversationPartnerDisplayName |
| 648 | skype | 1328256 | ✔ | TlvTypeSkypeChatMembers |
| 648 | skype | 1328512 | ✔ | TlvTypeSkypeTextMessage |
| 648 | skype | 1328768 | ✔ | TlvTypeSkypeChatID |
| 648 | skype | 1329024 | ✔ | TlvTypeSkypeSenderAccountName |
| 649 | skype | 1329280 | ✔ | TlvTypeSkypeSenderDisplayName |
| 649 | skype | 1329536 | ✔ | TlvTypeSkypeIncoming |
| 649 | skype | 1329792 | ✔ | TlvTypeSkypeSessionType |
| 704 | changed file | 1442208 | ✔ | TlvTypeChangedFileMetaInfo |
| 704 | changed file | 1442432 | ✔ | TlvTypeChangedFileChangeTime |
| 704 | changed file | 1442688 | ✔ | TlvTypeChangedFileChangeEvent |
| 704 | changed file | 1442960 | ✔ | TlvTypeChangedFileRecording |
| 710 | config changed | 1454240 | ✔ | TlvTypeGetChangedConfigRequest |
| 710 | config changed | 1454496 | ✔ | TlvTypeChangedConfigReply |
| 710 | config changed | 1454752 | ✔ | TlvTypeSetChangedConfigRequest |
| 710 | config changed | 1454912 | ✔ | TlvTypeConfigChangedEvents |
| 736 | | 1507744 | ✔ | TlvTypeAccessedFileMetaInfo |
| 736 | | 1507968 | ✔ | TlvTypeAccessedFileAccessTime |
| 736 | | 1508224 | ✔ | TlvTypeAccessedFileAccessEvent |
| 736 | | 1508496 | ✔ | TlvTypeAccessedFileRecording |
| 736 | | 1508736 | ✔ | TlvTypeAccessedApplicationName |
| 736 | | 1508912 | ✔ | TlvTypeConfigRecordImagesFromExplorer |
| 742 | accessed config | 1519776 | ✔ | TlvTypeGetAccessedConfigRequest |
| 742 | accessed config | 1520032 | ✔ | TlvTypeAccessedConfigReply |
| 742 | accessed config | 1520288 | ✔ | TlvTypeSetAccessedConfigRequest |
| 742 | accessed config | 1520448 | ✔ | TlvTypeConfigAccessedEvents |
| 768 | print | 1573280 | ✔ | TlvTypePrintFileMetaInfo |
| 768 | print | 1573520 | ✔ | TlvTypePrintFrame |
| 772 | print | 1581184 | ✔ | TlvTypePrintApplicationName |
| 772 | print | 1581440 | ✔ | TlvTypePrintFilename |
| 772 | print | 1581696 | ✔ | TlvTypePrintEncodingType |
| 774 | print config | 1585312 | ✔ | TlvTypeGetPrintConfigRequest |
| 774 | print config | 1585568 | ✔ | TlvTypePrintConfigReply |
| 774 | print config | 1585824 | ✔ | TlvTypeSetPrintConfigRequest |
| 800 | deleted | 1638816 | ✔ | TlvTypeDeletedFileMetaInfo |
| 800 | deleted | 1639296 | ✔ | TlvTypeDeletedFileDeletionTime |
| 800 | deleted | 1639552 | ✔ | TlvTypeDeletedFileRecycleBin |
| 800 | deleted | 1639808 | ✔ | TlvTypeDeletedMethod |
| 800 | deleted | 1640064 | ✔ | TlvTypeDeletedApplicationName |
| 800 | deleted | 1640336 | ✔ | TlvTypeDeletedFileRecording |
| 806 | config deleted | 1650848 | ✔ | TlvTypeGetDeletedConfigRequest |
| 806 | config deleted | 1651104 | ✔ | TlvTypeDeletedConfigReply |
| 806 | config deleted | 1651360 | ✔ | TlvTypeSetDeletedConfigRequest |
| 1024 | application upload forensics | 2097568 | ✔ | TlvTypeUploadForensicsApplicationRequest |
| 1024 | application upload forensics | 2097824 | ✔ | TlvTypeUploadForensicsApplicationReply |
| 1024 | application upload forensics | 2098080 | ✔ | TlvTypeUploadForensicsApplicationChunk |
| 1024 | application upload forensics | 2098336 | ✔ | TlvTypeUploadForensicsApplicationDoneRequest |
| 1024 | application upload forensics | 2098592 | ✔ | TlvTypeUploadForensicsApplicationDoneReply |
| 1026 | application remove forensics | 2101664 | ✔ | TlvTypeRemoveForensicsApplicationRequest |
| 1026 | application remove forensics | 2101920 | ✔ | TlvTypeRemoveForensicsApplicationReply |
| 1028 | app forensics execute | 2105760 | ✔ | TlvTypeForensicsAppExecuteRequest |
| 1028 | app forensics execute | 2106016 | ✔ | TlvTypeForensicsAppExecuteReply |
| 1028 | app forensics execute | 2106272 | ✔ | TlvTypeForensicsAppExecuteResult |
| 1028 | app forensics execute | 2106528 | ✔ | TlvTypeForensicsAppExecuteResultChunk |
| 1028 | app forensics execute | 2106784 | ✔ | TlvTypeForensicsAppExecuteResultDone |
| 1028 | app forensics execute | 2107040 | ✔ | TlvTypeForensicsCancelAppExecuteRequest |
| 1028 | app forensics execute | 2107296 | ✔ | TlvTypeForensicsCancelAppExecuteReply |
| 1030 | config forensics | 2109600 | ✔ | TlvTypeGetForensicsConfigRequest |
| 1030 | config forensics | 2109856 | ✔ | TlvTypeForensicsConfigReply |
| 1030 | config forensics | 2110112 | ✔ | TlvTypeSetForensicsConfigRequest |
| 1032 | application config info forensics | 2113680 | ✔ | TlvTypeConfigForensicsApplicationInfoGeneric |
| 1032 | application config info forensics | 2113952 | ✔ | TlvTypeConfigForensicsApplicationInfo |
| 1034 | forensics | 2117760 | ✔ | TlvTypeConfigForensicsApplicationName |
| 1034 | forensics | 2117952 | ✔ | TlvTypeConfigForensicsApplicationSize |
| 1034 | forensics | 2118208 | ✔ | TlvTypeConfigForensicsApplicationID |
| 1034 | forensics | 2118528 | ✔ | TlvTypeConfigForensicsApplicationCmdline |
| 1034 | forensics | 2118784 | ✔ | TlvTypeConfigForensicsApplicationOutput |
| 1034 | forensics | 2118976 | ✔ | TlvTypeConfigForensicsApplicationTimeout |
| 1034 | forensics | 2119232 | ✔ | TlvTypeConfigForensicsApplicationVersion |
| 1034 | forensics | 2119552 | ✔ | TlvTypeForensicsFriendlyName |
| 1035 | output application config forensics | 2119808 | ✔ | TlvTypeConfigForensicsApplicationOutputPrepend |
| 1035 | output application config forensics | 2120064 | ✔ | TlvTypeConfigForensicsApplicationOutputContentType |
| 1056 | vo meta info ip | 2163104 | ✔ | TlvTypeVoIPMetaInfo |
| 1058 | vo ip | 2166912 | ✔ | TlvTypeVoIPEncodingType |
| 1058 | vo ip | 2167168 | ✔ | TlvTypeVoIPSessionType |
| 1058 | vo ip | 2167424 | ✔ | TlvTypeVoIPApplicationName |
| 1058 | vo ip | 2167696 | ✔ | TlvTypeVoIPAppScreenshot |
| 1058 | vo ip | 2167952 | ✔ | TlvTypeVoIPAudioRecording |
| 1058 | vo ip | 2168112 | ✔ | TlvTypeConfigVoIPScreenshotEnabled |
| 1062 | vo config ip | 2175136 | ✔ | TlvTypeGetVoIPConfigRequest |
| 1062 | vo config ip | 2175392 | ✔ | TlvTypeVoIPConfigReply |
| 1062 | vo config ip | 2175648 | ✔ | TlvTypeSetVoIPConfigRequest |
| 1088 | clicks mouse | 2228640 | ✔ | TlvTypeMouseClicksMetaInfo |
| 1088 | clicks mouse | 2228896 | ✔ | TlvTypeMouseClicksFrame |
| 1090 | clicks mouse | 2232448 | ✔ | TlvTypeMouseClicksEncodingType |
| 1090 | clicks mouse | 2232896 | ✔ | TlvTypeConfigMouseClicksRectangle |
| 1090 | clicks mouse | 2233152 | ✔ | TlvTypeConfigMouseClicksSensitivity |
| 1090 | clicks mouse | 2233408 | ✔ | TlvTypeConfigMouseClicksType |
| 1094 | clicks config mouse | 2240672 | ✔ | TlvTypeGetMouseClicksConfigRequest |
| 1094 | clicks config mouse | 2240928 | ✔ | TlvTypeMouseClicksConfigReply |
| 1094 | clicks config mouse | 2241184 | ✔ | TlvTypeSetMouseClicksConfigRequest |
| 2112 | sms | 4325792 | ✔ | TlvTypeMobileSMSMetaInfo |
| 2112 | sms | 4326016 | ✔ | TlvTypeMobileSMSData |
| 2112 | sms | 4326256 | ✔ | TlvTypeSMSSenderNumber |
| 2112 | sms | 4326512 | ✔ | TlvTypeSMSRecipientNumber |
| 2112 | sms | 4326528 | ✔ | TlvTypeSMSInformation |
| 2112 | sms | 4326768 | ✔ | TlvTypeSMSDirection |
| 2112 | sms | 4327040 | × | unknown |
| 2144 | address book mobile | 4391328 | ✔ | TlvTypeMobileAddressBookMetaInfo |
| 2144 | address book mobile | 4391552 | ✔ | TlvTypeMobileAddressBookData |
| 2152 | address book checksum mobile | 4407360 | ✔ | TlvTypeMobileAddressBookChecksum |
| 2176 | mobile blackberry | 4456864 | ✔ | TlvTypeMobileBlackberryMessengerMetaInfo |
| 2176 | mobile blackberry | 4457088 | ✔ | TlvTypeMobileBlackberryMessengerData |
| 2176 | mobile blackberry | 4457328 | ✔ | TlvTypeMobileBlackberryMsChatID |
| 2176 | mobile blackberry | 4457600 | ✔ | TlvTypeMobileBlackberryMsConversationPartners |
| 2208 | mobile tracking | 4522400 | ✔ | TlvTypeMobileTrackingStartRequest |
| 2208 | mobile tracking | 4522656 | ✔ | TlvTypeMobileTrackingStopRequest |
| 2208 | mobile tracking | 4523376 | ✔ | TlvTypeMobileTrackingDataV10 |
| 2214 | mobile config tracking | 4535200 | ✔ | TlvTypeMobileTrackingConfig |
| 2214 | mobile config tracking | 4535440 | ✔ | TlvTypeMobileTrackingConfigRaw |
| 2216 | mobile tracking | 4538432 | ✔ | TlvTypeMobileTrackingTimeInterval |
| 2216 | mobile tracking | 4538688 | ✔ | TlvTypeMobileTrackingDistance |
| 2216 | mobile tracking | 4538928 | ✔ | TlvTypeMobileTrackingSendOnAnyChannel |
| 2240 | mobile call phone | 4587936 | ✔ | TlvTypeMobilePhoneCallLogsMetaInfo |
| 2240 | mobile call phone | 4588192 | ✔ | TlvTypeMobilePhoneCallLogsData |
| 2240 | mobile call phone | 4588400 | ✔ | TlvTypeMobilePhoneCallLogsType |
| 2240 | mobile call phone | 4588672 | ✔ | TlvTypeMobilePhoneCallAdditionalInformation |
| 2240 | mobile call phone | 4588912 | ✔ | TlvTypeMobilePhoneCallLogsCallerNumber |
| 2240 | mobile call phone | 4589168 | ✔ | TlvTypeMobilePhoneCallLogsCalleeNumber |
| 2240 | mobile call phone | 4589440 | ✔ | TlvTypeMobilePhoneCallLogsCallerName |
| 2241 | name call phone logs mobile callee | 4589696 | ✔ | TlvTypeMobilePhoneCallLogsCalleeName |
| 2242 | last call phone entry mobile endtime log | 4591680 | ✔ | TlvTypeMobilePhoneCallLogLastEntryEndtime |
| 3072 | mobile logging | 6291872 | ✔ | TlvTypeMobileLoggingMetaInfo |
| 3072 | mobile logging | 6292096 | ✔ | TlvTypeMobileLoggingData |
| 3616 | master agent | 7405984 | ✔ | TlvTypeMasterAgentLogin |
| 3616 | master agent | 7406240 | ✔ | TlvTypeMasterAgentLoginAnswer |
| 3616 | master agent | 7406752 | ✔ | TlvTypeMasterAgentTargetList |
| 3616 | master agent | 7407008 | ✔ | TlvTypeMasterAgentTargetOnlineList |
| 3616 | master agent | 7407264 | ✔ | TlvTypeMasterAgentTargetInfoReply |
| 3616 | master agent | 7407520 | ✔ | TlvTypeMasterAgentUserList |
| 3617 | master agent list | 7407776 | ✔ | TlvTypeMasterAgentUserListReply |
| 3617 | master agent list | 7408032 | ✔ | TlvTypeMasterAgentTargetArchivedList |
| 3617 | master agent list | 7408288 | ✔ | TlvTypeMasterAgentTargetListEx |
| 3617 | master agent list | 7408544 | ✔ | TlvTypeMasterAgentTargetOnlineListEx |
| 3617 | master agent list | 7408800 | ✔ | TlvTypeMasterAgentMobileTargetArchivedList |
| 3617 | master agent list | 7409056 | ✔ | TlvTypeMasterAgentMobileTargetList |
| 3617 | master agent list | 7409312 | ✔ | TlvTypeMasterAgentMobileTargetOnlineList |
| 3618 | | 7409824 | ✔ | TlvTypeMasterAgentQueryFirst |
| 3618 | | 7410080 | ✔ | TlvTypeMasterAgentQueryNext |
| 3618 | | 7410336 | ✔ | TlvTypeMasterAgentQueryLast |
| 3618 | | 7410592 | ✔ | TlvTypeMasterAgentQueryAnswer |
| 3618 | | 7410848 | ✔ | TlvTypeMasterAgentRemoveRecord |
| 3618 | | 7411104 | ✔ | TlvTypeMasterAgentTargetInfoExReply |
| 3618 | | 7411344 | ✔ | TlvTypeTargetInfoExProperty |
| 3618 | | 7411616 | ✔ | TlvTypeTargetInfoExPropertyValue |
| 3619 | | 7411840 | ✔ | TlvTypeTargetInfoExPropertyValueName |
| 3619 | | 7411968 | ✔ | TlvTypeTargetInfoExPropertyValueData |
| 3619 | | 7412384 | ✔ | TlvTypeMasterAgentAlarm |
| 3620 | master agent | 7413920 | ✔ | TlvTypeMasterAgentRetrieveData |
| 3620 | master agent | 7414176 | ✔ | TlvTypeMasterAgentRetrieveDataAnswer |
| 3620 | master agent | 7414432 | ✔ | TlvTypeMasterAgentRemoveUser |
| 3620 | master agent | 7414688 | ✔ | TlvTypeMasterAgentRemoveTarget |
| 3620 | master agent | 7414944 | ✔ | TlvTypeMasterAgentRetrieveDataComments |
| 3620 | master agent | 7415200 | ✔ | TlvTypeMasterAgentUpdateDataComments |
| 3620 | master agent | 7415712 | ✔ | TlvTypeMasterAgentRetrieveActivityLogging |
| 3621 | master agent | 7415968 | ✔ | TlvTypeMasterAgentRetrieveMasterLogging |
| 3621 | master agent | 7416224 | ✔ | TlvTypeMasterAgentRetrieveAgentActivityLogging |
| 3621 | master agent | 7417248 | ✔ | TlvTypeMasterAgentSendUserGUIConfig |
| 3621 | master agent | 7417504 | ✔ | TlvTypeMasterAgentGetUserGUIConfigRequest |
| 3621 | master agent | 7417760 | ✔ | TlvTypeMasterAgentGetUserGUIConfigReply |
| 3622 | master agent | 7418016 | ✔ | TlvTypeMasterAgentProxyList |
| 3622 | master agent | 7418272 | ✔ | TlvTypeMasterAgentProxyInfoReply |
| 3622 | master agent | 7419040 | ✔ | TlvTypeMasterAgentNameValuePacket |
| 3622 | master agent | 7419248 | ✔ | TlvTypeMasterAgentValueName |
| 3622 | master agent | 7419392 | ✔ | TlvTypeMasterAgentValueData |
| 3622 | master agent | 7419808 | ✔ | TlvTypeMasterAgentRetrieveTargetHistory |
| 3623 | install master agent | 7421088 | ✔ | TlvTypeMasterAgentInstallMasterLicense |
| 3623 | install master agent | 7421344 | ✔ | TlvTypeMasterAgentInstallSoftwareUpdate |
| 3623 | install master agent | 7421600 | ✔ | TlvTypeMasterAgentInstallSoftwareUpdateChunk |
| 3623 | install master agent | 7421856 | ✔ | TlvTypeMasterAgentInstallSoftwareUpdateDone |
| 3624 | master agent | 7422112 | ✔ | TlvTypeMasterAgentSoftwareUpdateInfo |
| 3624 | master agent | 7422368 | ✔ | TlvTypeMasterAgentSoftwareUpdateInfoReply |
| 3624 | master agent | 7422624 | ✔ | TlvTypeMasterAgentSoftwareUpdate |
| 3624 | master agent | 7422880 | ✔ | TlvTypeMasterAgentSoftwareUpdateReply |
| 3624 | master agent | 7423136 | ✔ | TlvTypeMasterAgentSoftwareUpdateNext |
| 3624 | master agent | 7423392 | ✔ | TlvTypeMasterAgentAddTimeSchedule |
| 3624 | master agent | 7423648 | ✔ | TlvTypeMasterAgentAddScreenSchedule |
| 3624 | master agent | 7423904 | ✔ | TlvTypeMasterAgentAddLockedSchedule |
| 3625 | master agent | 7424160 | ✔ | TlvTypeMasterAgentRemoveSchedule |
| 3625 | master agent | 7424416 | ✔ | TlvTypeMasterAgentGetSchedulerList |
| 3625 | master agent | 7424672 | ✔ | TlvTypeMasterAgentSchedulerTimeAction |
| 3625 | master agent | 7424928 | ✔ | TlvTypeMasterAgentSchedulerScreenAction |
| 3625 | master agent | 7425184 | ✔ | TlvTypeMasterAgentSchedulerLockedAction |
| 3625 | master agent | 7425440 | ✔ | TlvTypeMasterAgentProjectSoftwareUpdateInfo |
| 3625 | master agent | 7425696 | ✔ | TlvTypeMasterAgentProjectSoftwareUpdateInfoReply |
| 3625 | master agent | 7425952 | ✔ | TlvTypeMasterAgentProjectSoftwareUpdate |
| 3626 | master agent | 7426112 | ✔ | TlvTypeMasterAgentSchedulerID |
| 3626 | master agent | 7426368 | ✔ | TlvTypeMasterAgentSchedulerStartTime |
| 3626 | master agent | 7426624 | ✔ | TlvTypeMasterAgentSchedulerStopTime |
| 3626 | master agent | 7427488 | ✔ | TlvTypeMasterAgentAddRecordedDataAvailableSchedule |
| 3626 | master agent | 7427744 | ✔ | TlvTypeMasterAgentSchedulerRecordedDataAvailableAction |
| 3627 | master agent data | 7428256 | ✔ | TlvTypeMasterAgentRetrieveRemoteMasterData |
| 3627 | master agent data | 7428512 | ✔ | TlvTypeMasterAgentRetrieveRemoteMasterDataReply |
| 3627 | master agent data | 7428768 | ✔ | TlvTypeMasterAgentDeleteRemoteMasterData |
| 3627 | master agent data | 7429024 | ✔ | TlvTypeMasterAgentRetrieveOfflineMasterData |
| 3627 | master agent data | 7429280 | ✔ | TlvTypeMasterAgentRetrieveOfflineMasterDataReply |
| 3627 | master agent data | 7429536 | ✔ | TlvTypeMasterAgentDeleteOfflineMasterData |
| 3628 | master agent | 7430304 | ✔ | TlvTypeMasterAgentQueryFirstEx |
| 3628 | master agent | 7430560 | ✔ | TlvTypeMasterAgentQueryNextEx |
| 3628 | master agent | 7430816 | ✔ | TlvTypeMasterAgentQueryLastEx |
| 3628 | master agent | 7431072 | ✔ | TlvTypeMasterAgentQueryAnswerEx |
| 3628 | master agent | 7431328 | ✔ | TlvTypeMasterAgentSendUserPreferences |
| 3628 | master agent | 7431584 | ✔ | TlvTypeMasterAgentGetUserPreferencesRequest |
| 3628 | master agent | 7431840 | ✔ | TlvTypeMasterAgentGetUserPreferencesReply |
| 3628 | master agent | 7432096 | ✔ | TlvTypeMasterAgentListMCFilesRequest |
| 3629 | master agent mc | 7432608 | ✔ | TlvTypeMasterAgentDeleteMCFiles |
| 3629 | master agent mc | 7432864 | ✔ | TlvTypeMasterAgentSendMCFiles |
| 3629 | master agent mc | 7433120 | ✔ | TlvTypeMasterAgentMCStatisticsRequest |
| 3629 | master agent mc | 7433376 | ✔ | TlvTypeMasterAgentMCStatisticsReply |
| 3629 | master agent mc | 7433616 | ✔ | TlvTypeMasterAgentMCStatisticsValues |
| 3630 | master agent | 7434400 | ✔ | TlvTypeMasterAgentTrojanKeyRequest |
| 3630 | master agent | 7434656 | ✔ | TlvTypeMasterAgentTrojanKeyReply |
| 3630 | master agent | 7434912 | ✔ | TlvTypeMasterAgentEvProtectionX509Request |
| 3630 | master agent | 7435168 | ✔ | TlvTypeMasterAgentEvProtectionX509Reply |
| 3630 | master agent | 7435424 | ✔ | TlvTypeMasterAgentEvProtectionImportCert |
| 3630 | master agent | 7435680 | ✔ | TlvTypeMasterAgentEvProtectionImportCertCompleted |
| 3630 | master agent | 7435936 | ✔ | TlvTypeMasterAgentConfigurationRequest |
| 3630 | master agent | 7436192 | ✔ | TlvTypeMasterAgentConfigurationReply |
| 3631 | master agent configuration | 7436448 | ✔ | TlvTypeMasterAgentConfigurationUpdateRequest |
| 3631 | master agent configuration | 7436704 | ✔ | TlvTypeMasterAgentConfigurationUpdateRequestCompleted |
| 3631 | master agent configuration | 7436944 | ✔ | TlvTypeMasterAgentConfiguration |
| 3631 | master agent configuration | 7437216 | ✔ | TlvTypeMasterAgentConfigurationValue |
| 3631 | master agent configuration | 7437424 | ✔ | TlvTypeMasterAgentConfigurationValueName |
| 3631 | master agent configuration | 7437568 | ✔ | TlvTypeMasterAgentConfigurationValueData |
| 3631 | master agent configuration | 7437984 | ✔ | TlvTypeMasterAgentConfigurationTransferDone |
| 3632 | master agent | 7438496 | ✔ | TlvTypeMasterAgentRetrieveTargetFile |
| 3632 | master agent | 7438752 | ✔ | TlvTypeMasterAgentRetrieveTargetFileAnswer |
| 3632 | master agent | 7438912 | ✔ | TlvTypeMasterAgentAlarmEntryID |
| 3632 | master agent | 7439168 | ✔ | TlvTypeMasterAgentAlarmEntryVersion |
| 3632 | master agent | 7439424 | ✔ | TlvTypeMasterAgentAlarmTriggerFlags |
| 3632 | master agent | 7439776 | ✔ | TlvTypeMasterAgentGetAlarmList |
| 3632 | master agent | 7440032 | ✔ | TlvTypeMasterAgentAddAlarmEntry |
| 3632 | master agent | 7440288 | ✔ | TlvTypeMasterAgentRemoveAlarmEntry |
| 3633 | master agent | 7440544 | ✔ | TlvTypeMasterAgentAlarmEntry |
| 3633 | master agent | 7440800 | ✔ | TlvTypeMasterAgentSystemStatus |
| 3633 | master agent | 7441056 | ✔ | TlvTypeMasterAgentSystemStatusRequest |
| 3633 | master agent | 7441312 | ✔ | TlvTypeMasterAgentSystemStatusReply |
| 3633 | master agent | 7441552 | ✔ | TlvTypeMasterAgentLicenseValues |
| 3633 | master agent | 7441824 | ✔ | TlvTypeMasterAgentLicenseValuesRequest |
| 3633 | master agent | 7442080 | ✔ | TlvTypeMasterAgentLicenseValuesReply |
| 3634 | master agent | 7442592 | ✔ | TlvTypeMasterAgentGetNetworkConfigurationRequest |
| 3634 | master agent | 7442848 | ✔ | TlvTypeMasterAgentSetNetworkConfigurationRequest |
| 3634 | master agent | 7443104 | ✔ | TlvTypeMasterAgentSetNetworkConfigurationReply |
| 3634 | master agent | 7443360 | ✔ | TlvTypeMasterAgentRetrieveAllowedModulesList |
| 3634 | master agent | 7443616 | ✔ | TlvTypeMasterAgentRetrieveAllowedModulesListAnswer |
| 3636 | master agent | 7446688 | ✔ | TlvTypeMasterAgentRemoveAllTargetData |
| 3636 | master agent | 7446944 | ✔ | TlvTypeMasterAgentForceDownloadRecordedData |
| 3636 | master agent | 7447200 | ✔ | TlvTypeMasterAgentTargetCreateNotification |
| 3636 | master agent | 7447456 | ✔ | TlvTypeMasterAgentMobileTargetInfoReply |
| 3636 | master agent | 7447696 | ✔ | TlvTypeMasterAgentMobileTargetInfoValues |
| 3638 | master agent alert | 7450784 | ✔ | TlvTypeMasterAgentAlert |
| 3640 | master agent | 7454880 | ✔ | TlvTypeMasterAgentAddUser |
| 3640 | master agent | 7455392 | ✔ | TlvTypeMasterAgentAddUserReply |
| 3640 | master agent | 7455648 | ✔ | TlvTypeMasterAgentModifyUser |
| 3640 | master agent | 7455904 | ✔ | TlvTypeMasterAgentSetUserPermission |
| 3640 | master agent | 7456160 | ✔ | TlvTypeMasterAgentSetTargetPermission |
| 3640 | master agent | 7456400 | ✔ | TlvTypeMasterAgentUserPermission |
| 3640 | master agent | 7456656 | ✔ | TlvTypeMasterAgentTargetPermission |
| 3641 | master agent | 7456928 | ✔ | TlvTypeMasterAgentUserPermissionValuePacket |
| 3641 | master agent | 7457184 | ✔ | TlvTypeMasterAgentTargetPermissionValuePacket |
| 3641 | master agent | 7457344 | ✔ | TlvTypeMasterAgentUserPermissionValueName |
| 3641 | master agent | 7457600 | ✔ | TlvTypeMasterAgentTargetPermissionValueName |
| 3641 | master agent | 7457856 | ✔ | TlvTypeMasterAgentUserPermissionValueData |
| 3641 | master agent | 7458112 | ✔ | TlvTypeMasterAgentTargetPermissionValueData |
| 3641 | master agent | 7458464 | ✔ | TlvTypeMasterAgentModifyPassword |
| 3641 | master agent | 7458656 | ✔ | TlvTypeMasterAgentMobileTargetPermissionValueName |
| 3642 | master agent | 7458976 | ✔ | TlvTypeMasterAgentUploadFile |
| 3642 | master agent | 7459232 | ✔ | TlvTypeMasterAgentUploadFileChunk |
| 3642 | master agent | 7459488 | ✔ | TlvTypeMasterAgentUploadFileDone |
| 3642 | master agent | 7459744 | ✔ | TlvTypeMasterAgentUploadFilesTransferDone |
| 3642 | master agent | 7460000 | ✔ | TlvTypeMasterAgentGetTargetModuleConfigRequest |
| 3642 | master agent | 7460256 | ✔ | TlvTypeMasterAgentRemoveFile |
| 3642 | master agent | 7460512 | ✔ | TlvTypeMasterAgentMobileProxyList |
| 3642 | master agent | 7460768 | ✔ | TlvTypeMasterAgentSMSProxyList |
| 3643 | master agent | 7461024 | ✔ | TlvTypeMasterAgentSMSProxyInfoReply |
| 3643 | master agent | 7461280 | ✔ | TlvTypeMasterAgentCallPhoneNumberList |
| 3643 | master agent | 7461536 | ✔ | TlvTypeMasterAgentCallPhoneNumberInfoReply |
| 3643 | master agent | 7461792 | ✔ | TlvTypeMasterAgentGetMobileTargetModuleConfigRequest |
| 3643 | master agent | 7462048 | ✔ | TlvTypeMasterAgentSendSMS |
| 3647 | master agent | 7469984 | ✔ | TlvTypeMasterAgentEncryptionRequired |
| 3647 | master agent | 7470240 | ✔ | TlvTypeMasterAgentFileCompleted |
| 3647 | master agent | 7470496 | ✔ | TlvTypeMasterAgentRequestCompleted |
| 3647 | master agent | 7470752 | ✔ | TlvTypeAgentMasterComm |
| 3647 | master agent | 7471008 | ✔ | TlvTypeMasterAgentRequestStatus |
| 3648 | master | 7471424 | ✔ | TlvTypeProxyMasterCommSig |
| 3648 | master | 7471520 | ✔ | TlvTypeMasterTargetConn |
| 3648 | master | 7471776 | ✔ | TlvTypeProxyMasterComm |
| 3648 | master | 7472032 | ✔ | TlvTypeMasterProxyComm |
| 3648 | master | 7472288 | ✔ | TlvTypeProxyMasterHeartBeatAnswer |
| 3648 | master | 7472544 | ✔ | TlvTypeProxyMasterDisconnect |
| 3648 | master | 7472704 | ✔ | TlvTypeProxyMasterNotification |
| 3648 | master | 7473056 | ✔ | TlvTypeProxyMasterRequest |
| 3649 | master | 7473312 | ✔ | TlvTypeMasterProxyCommNotification |
| 3649 | master | 7473568 | ✔ | TlvTypeMasterCheckTargetDisconnect |
| 3680 | target proxy | 7536960 | ✔ | TlvTypeProxyTargetCommSig |
| 3680 | target proxy | 7537312 | ✔ | TlvTypeProxyTargetComm |
| 3680 | target proxy | 7537568 | ✔ | TlvTypeProxyMasterTargetComm |
| 3680 | target proxy | 7537728 | ✔ | TlvTypeProxyTargetRequestCrypto |
| 3680 | target proxy | 7538064 | ✔ | TlvTypeProxyTargetAnswerCrypto |
| 3744 | target | 7668128 | ✔ | TlvTypeMasterTargetComm |
| 3744 | target | 7668384 | ✔ | TlvTypeTargetCloseAllLiveStreaming |
| 3776 | relay | 7733664 | ✔ | TlvTypeRelayProxyComm |
| 3776 | relay | 7734176 | ✔ | TlvTypeRelayDummyHeartbeat |
| 4032 | test type meta | 8257792 | ✔ | TlvTypeTestMetaTypeInvalid |
| 4032 | test type meta | 8258608 | ✔ | TlvTypeTestMetaTypeBool |
| 4032 | test type meta | 8258880 | ✔ | TlvTypeTestMetaTypeUInt |
| 4032 | test type meta | 8259152 | ✔ | TlvTypeTestMetaTypeInt |
| 4032 | test type meta | 8259440 | ✔ | TlvTypeTestMetaTypeString |
| 4033 | test | 8259712 | ✔ | TlvTypeTestMetaTypeUnicode |
| 4033 | test | 8259984 | ✔ | TlvTypeTestMetaTypeRaw |
| 4033 | test | 8260256 | ✔ | TlvTypeTestMetaTypeGroup |
| 4033 | test | 8260416 | ✔ | TlvTypeTestMemberIdentifier |
| 4033 | test | 8260736 | ✔ | TlvTypeTestMemberName |
| 4096 | target | 8389008 | ✔ | TlvTypeTargetData |
| 4096 | target | 8389280 | ✔ | TlvTypeTargetHeartBeat |
| 4096 | target | 8389680 | ✔ | TlvTypeTargetKeepSessionAlive |
| 4096 | target | 8390000 | ✔ | TlvTypeTargetLocalIP |
| 4096 | target | 8390256 | ✔ | TlvTypeTargetGlobalIP |
| 4096 | target | 8390448 | ✔ | TlvTypeTargetState |
| 4097 | agent master | 8390784 | ✔ | TlvTypeTargetID |
| 4097 | agent master | 8391072 | ✔ | TlvTypeGetInstalledModulesRequest |
| 4097 | agent master | 8391328 | ✔ | TlvTypeInstalledModulesReply |
| 4097 | agent master | 8391488 | ✔ | TlvTypeTrojanUID |
| 4097 | agent master | 8391808 | ✔ | TlvTypeTrojanID |
| 4097 | agent master | 8392000 | ✔ | TlvTypeTrojanMaxInfections |
| 4097 | agent master | 8392240 | ✔ | TlvTypeScreenSaverOn |
| 4097 | agent master | 8392496 | ✔ | TlvTypeScreenLocked |
| 4098 | agent master | 8392752 | ✔ | TlvTypeRecordedDataAvailable |
| 4098 | agent master | 8393024 | ✔ | TlvTypeDownloadedRecordedDataTimeStamp |
| 4098 | agent master | 8393280 | ✔ | TlvTypeInstallationMode |
| 4098 | agent master | 8393552 | ✔ | TlvTypeTargetRemoveNotification |
| 4098 | agent master | 8393792 | ✔ | TlvTypeTargetPlatformBits |
| 4098 | agent master | 8394032 | ✔ | TlvTypeRemoveItselfMaxInfectionReached |
| 4098 | agent master | 8394288 | ✔ | TlvTypeRemoveItselfAtMasterRequest |
| 4098 | agent master | 8394544 | ✔ | TlvTypeRemoveItselfAtAgentRequest |
| 4099 | agent master | 8394912 | ✔ | TlvTypeRemoveItselfAtAgentReqRequest |
| 4099 | agent master | 8395072 | ✔ | TlvTypeRecordedFilesDownloadTotal |
| 4099 | agent master | 8395328 | ✔ | TlvTypeRecordedFilesDownloadProgress |
| 4099 | agent master | 8395632 | ✔ | TlvTypeTargetLicenseInfo |
| 4099 | agent master | 8395840 | ✔ | TlvTypeRemoveTargetLicenseInfo |
| 4099 | agent master | 8396176 | ✔ | TlvTypeTargetAllConfigurations |
| 4100 | target error | 8396960 | ✔ | TlvTypeTargetError |
| 4102 | target config | 8401056 | ✔ | TlvTypeGetTargetConfigRequest |
| 4102 | target config | 8401312 | ✔ | TlvTypeTargetConfigReply |
| 4102 | target config | 8401568 | ✔ | TlvTypeSetTargetConfigRequest |
| 4102 | target config | 8402304 | ✔ | TlvTypeConfigTargetID |
| 4102 | target config | 8402496 | ✔ | TlvTypeConfigTargetHeartbeatInterval |
| 4102 | target config | 8402800 | ✔ | TlvTypeConfigTargetProxy |
| 4103 | agent master | 8403008 | ✔ | TlvTypeConfigTargetPort |
| 4103 | agent master | 8403584 | ✔ | TlvTypeConfigAutoRemovalDateTime |
| 4103 | agent master | 8403776 | ✔ | TlvTypeConfigAutoRemovalIfNoProxy |
| 4103 | agent master | 8404032 | ✔ | TlvTypeInternalAutoRemovalElapsedTime |
| 4104 | active hiding config | 8405040 | ✔ | TlvTypeConfigActiveHiding |
| 4106 | target module | 8409248 | ✔ | TlvTypeTargetLoadModuleRequest |
| 4106 | target module | 8409504 | ✔ | TlvTypeTargetLoadModuleReply |
| 4106 | target module | 8409760 | ✔ | TlvTypeTargetUnLoadModuleRequest |
| 4106 | target module | 8410016 | ✔ | TlvTypeTargetUnLoadModuleReply |
| 4106 | target module | 8410272 | ✔ | TlvTypeTargetUploadModuleRequest |
| 4106 | target module | 8410528 | ✔ | TlvTypeTargetUploadModuleReply |
| 4106 | target module | 8410784 | ✔ | TlvTypeTargetUploadModuleChunk |
| 4106 | target module | 8411040 | ✔ | TlvTypeTargetUploadModuleDoneRequest |
| 4107 | target module | 8411296 | ✔ | TlvTypeTargetUploadModuleDoneReply |
| 4107 | target module | 8411552 | ✔ | TlvTypeTargetRemoveModuleRequest |
| 4107 | target module | 8411808 | ✔ | TlvTypeTargetRemoveModuleReply |
| 4107 | target module | 8412064 | ✔ | TlvTypeTargetOfflineUploadModuleRequest |
| 4107 | target module | 8412320 | ✔ | TlvTypeTargetOfflineUploadModuleReply |
| 4107 | target module | 8412576 | ✔ | TlvTypeTargetOfflineUploadModuleChunk |
| 4107 | target module | 8412832 | ✔ | TlvTypeTargetOfflineUploadModuleDoneRequest |
| 4107 | target module | 8413088 | ✔ | TlvTypeTargetOfflineUploadModuleDoneReply |
| 4108 | target error | 8413344 | ✔ | TlvTypeTargetOfflineError |
| 4108 | target error | 8413600 | ✔ | TlvTypeTargetUploadError |
| 4109 | files reply master list agent mc | 8415392 | ✔ | TlvTypeMasterAgentListMCFilesReply |
| 4110 | target recorded | 8417440 | ✔ | TlvTypeTargetGetRecordedFilesRequest |
| 4110 | target recorded | 8417696 | ✔ | TlvTypeTargetRecordedFilesReply |
| 4110 | target recorded | 8417952 | ✔ | TlvTypeTargetRecordedFileDownloadRequest |
| 4110 | target recorded | 8418208 | ✔ | TlvTypeTargetRecordedFileDownloadReply |
| 4110 | target recorded | 8418464 | ✔ | TlvTypeTargetRecordedFileDownloadChunk |
| 4110 | target recorded | 8418720 | ✔ | TlvTypeTargetRecordedFileDownloadCompleted |
| 4110 | target recorded | 8418976 | ✔ | TlvTypeTargetRecordedFileDeleteRequest |
| 4110 | target recorded | 8419232 | ✔ | TlvTypeTargetRecordedFileDeleteReply |
| 4111 | target recorded ex | 8419488 | ✔ | TlvTypeTargetGetRecordedFilesRequestEx |
| 4111 | target recorded ex | 8419744 | ✔ | TlvTypeTargetRecordedFilesReplyEx |
| 4111 | target recorded ex | 8420000 | ✔ | TlvTypeTargetRecordedFileDeleteRequestEx |
| 4111 | target recorded ex | 8420256 | ✔ | TlvTypeTargetRecordedFilesDownloadRequestEx |
| 4128 | data | 8454544 | ✔ | TlvTypeProxyData |
| 4128 | data | 8454800 | ✔ | TlvTypeRelayData |
| 4130 | proxy | 8458400 | ✔ | TlvTypeProxyTargetDisconnect |
| 4130 | proxy | 8458656 | ✔ | TlvTypeProxyMobileTargetDisconnect |
| 4130 | proxy | 8458912 | ✔ | TlvTypeProxyDummyHeartbeat |
| 4130 | proxy | 8459168 | ✔ | TlvTypeProxyMobileDummyHeartbeat |
| 4160 | master | 8520080 | ✔ | TlvTypeMasterData |
| 4160 | master | 8520768 | ✔ | TlvTypeMasterMode |
| 4160 | master | 8521024 | ✔ | TlvTypeMasterToken |
| 4160 | master | 8521344 | ✔ | TlvTypeMasterQueryResult |
| 4161 | string master alarm | 8522368 | ✔ | TlvTypeMasterAlarmString |
| 4192 | agent | 8585616 | ✔ | TlvTypeAgentData |
| 4192 | agent | 8585808 | ✔ | TlvTypeAgentQueryID |
| 4192 | agent | 8586048 | ✔ | TlvTypeAgentQueryModSubmodID |
| 4192 | agent | 8586304 | ✔ | TlvTypeAgentQueryFromDate |
| 4192 | agent | 8586560 | ✔ | TlvTypeAgentQueryToDate |
| 4192 | agent | 8586816 | ✔ | TlvTypeAgentQuerySortOrder |
| 4192 | agent | 8587136 | ✔ | TlvTypeAgentQueryValueFilter |
| 4193 | uid agent | 8587328 | ✔ | TlvTypeAgentUID |
| 4224 | mobile | 8651152 | ✔ | TlvTypeMobileTargetData |
| 4224 | mobile | 8651376 | ✔ | TlvTypeMobileTargetHeartBeatV10 |
| 4224 | mobile | 8651632 | ✔ | TlvTypeMobileTargetExtendedHeartBeatV10 |
| 4224 | mobile | 8651888 | ✔ | TlvTypeMobileHeartBeatReplyV10 |
| 4225 | installed reply modules mobile | 8653472 | ✔ | TlvTypeMobileInstalledModulesReply |
| 4225 | installed reply modules mobile | 8652912 | × | unknown |
| 4226 | module upload mobile target | 8655008 | ✔ | TlvTypeMobileTargetOfflineUploadModuleRequest |
| 4226 | module upload mobile target | 8656032 | ✔ | TlvTypeMobileTargetUploadModuleRequest |
| 4226 | module upload mobile target | 8656288 | ✔ | TlvTypeMobileTargetUploadModuleReply |
| 4226 | module upload mobile target | 8656544 | ✔ | TlvTypeMobileTargetUploadModuleChunk |
| 4226 | module upload mobile target | 8656800 | ✔ | TlvTypeMobileTargetUploadModuleDoneRequest |
| 4227 | target mobile | 8657056 | ✔ | TlvTypeMobileTargetUploadModuleDoneReply |
| 4227 | target mobile | 8657312 | ✔ | TlvTypeMobileTargetRemoveModuleRequest |
| 4227 | target mobile | 8657568 | ✔ | TlvTypeMobileTargetRemoveModuleReply |
| 4227 | target mobile | 8657824 | ✔ | TlvTypeMobileTargetOfflineUploadModuleReply |
| 4227 | target mobile | 8658080 | ✔ | TlvTypeMobileTargetOfflineUploadModuleChunk |
| 4227 | target mobile | 8658336 | ✔ | TlvTypeMobileTargetOfflineUploadModuleDoneRequest |
| 4227 | target mobile | 8658592 | ✔ | TlvTypeMobileTargetOfflineUploadModuleDoneReply |
| 4227 | target mobile | 8658848 | ✔ | TlvTypeMobileTargetOfflineError |
| 4228 | mobile target | 8659104 | ✔ | TlvTypeMobileTargetError |
| 4228 | mobile target | 8659360 | ✔ | TlvTypeMobileTargetGetRecordedFilesRequest |
| 4228 | mobile target | 8659616 | ✔ | TlvTypeMobileTargetRecordedFilesReply |
| 4228 | mobile target | 8659872 | ✔ | TlvTypeMobileTargetRecordedFileDownloadRequest |
| 4228 | mobile target | 8660128 | ✔ | TlvTypeMobileTargetRecordedFileDownloadReply |
| 4228 | mobile target | 8660384 | ✔ | TlvTypeMobileTargetRecordedFileDownloadChunk |
| 4228 | mobile target | 8660640 | ✔ | TlvTypeMobileTargetRecordedFileDownloadCompleted |
| 4228 | mobile target | 8660896 | ✔ | TlvTypeMobileTargetRecordedFileDeleteRequest |
| 4229 | target reply delete mobile recorded file | 8661152 | ✔ | TlvTypeMobileTargetRecordedFileDeleteReply |
| 4230 | mobile config target | 8663968 | ✔ | TlvTypeMobileTargetOfflineConfig |
| 4230 | mobile config target | 8664224 | ✔ | TlvTypeMobileTargetEmergencyConfigAsTLV |
| 4230 | mobile config target | 8664432 | ✔ | TlvTypeMobileTargetEmergencyConfig |
| 4234 | load module mobile target | 8671392 | ✔ | TlvTypeMobileTargetLoadModuleRequest |
| 4234 | load module mobile target | 8671648 | ✔ | TlvTypeMobileTargetLoadModuleReply |
| 4234 | load module mobile target | 8671904 | ✔ | TlvTypeMobileTargetUnLoadModuleRequest |
| 4234 | load module mobile target | 8672160 | ✔ | TlvTypeMobileTargetUnLoadModuleReply |
| 4236 | target error | 8675472 | ✔ | TlvTypeMobileTargetHeartbeatEvents |
| 4236 | agent master files mc reply list | 8675648 | ✔ | TlvTypeMobileTargetHeartbeatInterval |
| 4236 | recorded target | 8675984 | ✔ | TlvTypeMobileTargetHeartbeatRestrictions |
| 4236 | recorded target | 8676208 | ✔ | TlvTypeConfigSMSPhoneNumber |
| 4236 | recorded target | 8676496 | ✔ | TlvTypeMobileTargetPositioning |
| 4236 | recorded target | 8676672 | ✔ | TlvTypeMobileTrojanUID |
| 4236 | recorded target | 8676976 | ✔ | TlvTypeMobileTrojanID |
| 4236 | recorded target | 8677296 | ✔ | TlvTypeMobileTargetLocationChangedRange |
| 4237 | config | 8677440 | ✔ | TlvTypeConfigMobileAutoRemovalDateTime |
| 4237 | config | 8677808 | ✔ | TlvTypeConfigOverwriteProxyAndPhones |
| 4237 | config | 8678000 | ✔ | TlvTypeConfigCallPhoneNumber |
| 4238 | ex recorded target | 8679488 | ✔ | TlvTypeLocationAreaCode |
| 4238 | ex recorded target | 8679744 | ✔ | TlvTypeCellID |
| 4238 | ex recorded target | 8680048 | ✔ | TlvTypeMobileCountryCode |
| 4238 | data | 8680304 | ✔ | TlvTypeMobileNetworkCode |
| 4238 | data | 8680560 | ✔ | TlvTypeIMSI |
| 4238 | proxy | 8680816 | ✔ | TlvTypeIMEI |
| 4238 | proxy | 8681072 | ✔ | TlvTypeGPSLatitude |
| 4238 | proxy | 8681328 | ✔ | TlvTypeGPSLongitude |
| 4239 | proxy | 8681520 | ✔ | TlvTypeFirstHeartbeat |
| 4239 | master | 8681872 | ✔ | TlvTypeInstalledModules |
| 4240 | gps valid values | 8683568 | ✔ | TlvTypeValidGPSValues |
| 4288 | mobile proxy comm target | 8782176 | ✔ | TlvTypeProxyMobileTargetCommSig |
| 4288 | mobile proxy comm target | 8782496 | ✔ | TlvTypeProxyMobileTargetComm |
| 4288 | mobile proxy comm target | 8782752 | ✔ | TlvTypeProxyMasterMobileTargetComm |
| 4384 | master mobile | 8978752 | ✔ | TlvTypeMobileProxyMasterCommSig |
| 4384 | master mobile | 8978848 | ✔ | TlvTypeMasterMobileTargetConn |
| 4384 | master mobile | 8979104 | ✔ | TlvTypeMobileProxyMasterComm |
| 4384 | master mobile | 8979360 | ✔ | TlvTypeMobileMasterProxyComm |
| 4384 | master mobile | 8979616 | ✔ | TlvTypeProxyMasterMobileHeartBeatAnswer |
| 4384 | master mobile | 8979872 | ✔ | TlvTypeMobileMasterProxyCommNotification |
| 8128 | agent | 16646544 | ✔ | TlvTypePlaintext |
| 8128 | agent uid | 16646800 | ✔ | TlvTypeCompression |
| 8128 | mobile | 16647056 | ✔ | TlvTypeEncryption |
| 8128 | mobile | 16647232 | ✔ | TlvTypeTargetUID |
| 8128 | mobile | 16647536 | ✔ | TlvTypeIPAddress |
| 8128 | mobile | 16647808 | ✔ | TlvTypeUserName |
| 8128 | installed reply modules mobile | 16648064 | ✔ | TlvTypeComputerName |
| 8129 | installed reply modules mobile | 16648304 | ✔ | TlvTypeLoginName |
| 8129 | module upload mobile target | 16648560 | ✔ | TlvTypePassphrase |
| 8129 | module upload mobile target | 16648832 | ✔ | TlvTypeRecordID |
| 8129 | module upload mobile target | 16649088 | ✔ | TlvTypeOwner |
| 8129 | module upload mobile target | 16649344 | ✔ | TlvTypeMetaData |
| 8129 | module upload mobile target | 16649536 | ✔ | TlvTypeModuleID |
| 8129 | mobile target | 16649856 | ✔ | TlvTypeOSName |
| 8129 | mobile target | 16650048 | ✔ | TlvTypeModuleSubID |
| 8130 | mobile target | 16650320 | ✔ | TlvTypeErrorCode |
| 8130 | mobile target | 16650560 | ✔ | TlvTypeOffset |
| 8130 | mobile target | 16650816 | ✔ | TlvTypeLength |
| 8130 | mobile target | 16651088 | ✔ | TlvTypeRequestID |
| 8130 | mobile target | 16651328 | ✔ | TlvTypeRequestType |
| 8130 | mobile target | 16651584 | ✔ | TlvTypeVersion |
| 8130 | mobile target | 16651840 | ✔ | TlvTypeMachineID |
| 8130 | mobile target | 16652096 | ✔ | TlvTypeMajorNumber |
| 8131 | mobile target | 16652352 | ✔ | TlvTypeMinorNumber |
| 8131 | mobile target | 16652656 | ✔ | TlvTypeGlobalIPAddress |
| 8131 | mobile target | 16652912 | ✔ | TlvTypeASCII_Filename |
| 8131 | mobile target | 16653120 | ✔ | TlvTypeFilesize |
| 8131 | mobile target | 16653392 | ✔ | TlvTypeFilecount |
| 8131 | mobile target | 16653712 | ✔ | TlvTypeFiledata |
| 8131 | target reply recorded delete file mobile | 16653968 | ✔ | TlvTypeMD5Sum |
| 8131 | mobile target config | 16654144 | ✔ | TlvTypeProxyPort |
| 8132 | mobile target config | 16654400 | ✔ | TlvTypeStatus |
| 8132 | mobile target config | 16654656 | ✔ | TlvTypeUserID |
| 8132 | module load mobile target | 16654912 | ✔ | TlvTypeGroupID |
| 8132 | module load mobile target | 16655168 | ✔ | TlvTypePermissions |
| 8132 | module load mobile target | 16655424 | ✔ | TlvTypeRequestCode |
| 8132 | module load mobile target | 16655680 | ✔ | TlvTypeDataSize |
| 8132 | | 16655936 | ✔ | TlvTypeKeyType |
| 8132 | | 16656240 | ✔ | TlvTypeEmail |
| 8133 | | 16656432 | ✔ | TlvTypeEnabled |
| 8133 | | 16656688 | ✔ | TlvTypeLicensed |
| 8133 | | 16656960 | ✔ | TlvTypeAudioFrequency |
| 8133 | | 16657216 | ✔ | TlvTypeAudioBitsPerSample |
| 8133 | | 16657472 | ✔ | TlvTypeAudioChannels |
| 8133 | | 16657728 | ✔ | TlvTypeStartTime |
| 8133 | config | 16657984 | ✔ | TlvTypeStopTime |
| 8133 | config | 16658240 | ✔ | TlvTypeBitMask |
| 8134 | config | 16658560 | ✔ | TlvTypeTimeZone |
| 8134 | | 16658816 | ✔ | TlvTypeDateTime |
| 8134 | | 16659072 | ✔ | TlvTypeStartSessionDateTime |
| 8134 | | 16659328 | ✔ | TlvTypeStopSessionDateTime |
| 8134 | | 16659520 | ✔ | TlvTypeDateTimeRef |
| 8134 | | 16659776 | ✔ | TlvTypeScheduleRepeat |
| 8134 | | 16660032 | ✔ | TlvTypeUnixMasterDateTime |
| 8134 | | 16660288 | ✔ | TlvTypeUnixUTCDateTime |
| 8135 | | 16660544 | ✔ | TlvTypeDurationInSeconds |
| 8135 | | 16660864 | ✔ | TlvTypeMasterRefTime |
| 8135 | | 16661120 | ✔ | TlvTypeMasterRefTimeStart |
| 8135 | values gps valid | 16661376 | ✔ | TlvTypeMasterRefTimeEnd |
| 8135 | | 16661568 | ✔ | TlvTypeCounter |
| 8135 | | 16661888 | ✔ | TlvTypeWhiteListEntry |
| 8135 | | 16662144 | ✔ | TlvTypeBlackListEntry |
| 8135 | | 16662336 | ✔ | TlvTypeBlackWhiteListingMode |
| 8136 | config | 16662576 | ✔ | TlvTypeConfigEnabled |
| 8136 | config | 16662848 | ✔ | TlvTypeConfigMaxRecordingSize |
| 8136 | config | 16663104 | ✔ | TlvTypeConfigAudioQuality |
| 8136 | config | 16663344 | ✔ | TlvTypeConfigVideoBlackAndWhite |
| 8136 | config | 16663616 | ✔ | TlvTypeConfigVideoResolution |
| 8136 | config | 16663872 | ✔ | TlvTypeConfigCaptureFrequency |
| 8136 | config | 16664128 | ✔ | TlvTypeConfigVideoQuality |
| 8136 | config | 16664384 | ✔ | TlvTypeConfigFilesStandardFilter |
| 8137 | config | 16664704 | ✔ | TlvTypeConfigFilesCustomFilter |
| 8137 | config | 16664896 | ✔ | TlvTypeConfigStandardLocation |
| 8137 | config | 16665216 | ✔ | TlvTypeConfigCustomLocation |
| 8137 | config | 16665408 | ✔ | TlvTypeConfigFileChunkSize |
| 8137 | config | 16665664 | ✔ | TlvTypeConfigFileTransferSpeed |
| 8137 | config | 16665904 | ✔ | TlvTypeConfigUploadFileOverwrite |
| 8137 | config | 16666160 | ✔ | TlvTypeConfigDeleteOverReboot |
| 8137 | config | 16666496 | ✔ | TlvTypeConfigCustomLocationException |
| 8138 | master mobile | 16666752 | ✔ | TlvTypeExtraData |
| 8138 | master mobile | 16667008 | ✔ | TlvTypeSignature |
| 8138 | | 16667264 | ✔ | TlvTypeComments |
| 8138 | | 16667520 | ✔ | TlvTypeDescription |
| 8138 | | 16667776 | ✔ | TlvTypeFilenameExtension |
| 8138 | | 16668032 | ✔ | TlvTypeSessionType |
| 8138 | | 16668224 | ✔ | TlvTypePeriod |
| 8138 | | 16668512 | ✔ | TlvTypeMobileTargetUID |
| 8139 | | 16668784 | ✔ | TlvTypeMobileTargetID |
| 8139 | | 16669072 | ✔ | TlvTypeMobilePlaintext |
| 8139 | | 16669328 | ✔ | TlvTypeMobileCompression |
| 8139 | | 16669584 | ✔ | TlvTypeMobileEncryption |
| 8139 | | 16669824 | ✔ | TlvTypeEncodingType |
| 8139 | | 16670576 | ✔ | TlvTypePhoneNumber |
| 8140 | custom config location mode | 16670784 | ✔ | TlvTypeConfigCustomLocationMode |
| 8140 | custom config location mode | 16672080 | × | unknown |
| 8140 | custom config location mode | 16671792 | × | unknown |
| 8142 | network interface | 16674928 | ✔ | TlvTypeNetworkInterface |
| 8142 | network interface | 16675136 | ✔ | TlvTypeNetworkInterfaceMode |
| 8142 | network interface | 16675440 | ✔ | TlvTypeNetworkInterfaceAddress |
| 8142 | network interface | 16675696 | ✔ | TlvTypeNetworkInterfaceNetmask |
| 8142 | network interface | 16675952 | ✔ | TlvTypeNetworkInterfaceGateway |
| 8142 | network interface | 16676208 | ✔ | TlvTypeNetworkInterfaceDNS_1 |
| 8142 | network interface | 16676464 | ✔ | TlvTypeNetworkInterfaceDNS_2 |
| 8143 | | 16677440 | ✔ | TlvTypeLoginTime |
| 8143 | | 16677696 | ✔ | TlvTypeLogoffTime |
| 8143 | | 16678720 | ✔ | TlvTypeGeneric_Type |
| 8144 | | 16678976 | ✔ | TlvTypeChecksum |
| 8144 | | 16679280 | ✔ | TlvTypeCity |
| 8144 | | 16679536 | ✔ | TlvTypeCountry |
| 8144 | | 16679792 | ✔ | TlvTypeCountryCode |
| 8146 | | 16683072 | ✔ | TlvTypeTargetType |
| 8146 | | 16683392 | ✔ | TlvTypeDurationString |
| 8146 | | 16683904 | × | unknown |
| 8146 | | 16684848 | × | unknown |
| 8160 | | 16712000 | ✔ | TlvTypeTargetConnectionBroken |
| 8160 | | 16712256 | ✔ | TlvTypeAgentConnectionBroken |
| 8160 | | 16712512 | ✔ | TlvTypeTargetOffline |
| 8176 | | 16744768 | ✔ | TlvTypeProxyConnectionBroken |
| 4242 | | 8688960 | × | unknown |
| 4242 | | 8689296 | × | unknown |
| 4242 | | 8689568 | × | unknown |
| 2752 | | 5636992 | × | unknown |
| 2752 | | 5637504 | × | unknown |
| 2752 | | 5637760 | × | unknown |
| 2752 | | 5636464 | × | unknown |
| 2752 | | 5636736 | × | unknown |
| 2752 | | 5637248 | × | unknown |
| 2753 | | 5638256 | × | unknown |
| 2753 | | 5638768 | × | unknown |
| 2754 | | 5641600 | × | unknown |
| 2754 | | 5640608 | × | unknown |
| 2754 | | 5641120 | × | unknown |
| 2754 | | 5640864 | × | unknown |
| 2754 | | 5640352 | × | unknown |
| 2218 | | 4542832 | × | unknown |
| 2218 | | 4542624 | × | unknown |
| 8147 | | 16685104 | × | unknown |
| 8147 | | 16685392 | × | unknown |
| 2658 | | 5444000 | × | unknown |
| 2658 | | 5444512 | × | unknown |
| 2656 | | 5440320 | × | unknown |
| 2656 | | 5439904 | × | unknown |
| 2660 | | 5447840 | × | unknown |
| 2722 | | 5575072 | × | unknown |
| 2722 | | 5575328 | × | unknown |
| 2722 | config | 5575840 | × | unknown |
| 2560 | config | 5243552 | × | unknown |
| 2560 | config | 5243296 | × | unknown |
| 4244 | config | 8693104 | × | unknown |
| 4244 | config | 8692080 | × | unknown |
| 4244 | config | 8692336 | × | unknown |
| 4244 | config | 8692592 | × | unknown |
| 4244 | config | 8692848 | × | unknown |
| 4244 | config | 8693360 | × | unknown |
| 4244 | config | 8691872 | × | unknown |
| 2690 | config | 5509536 | × | unknown |
| 2690 | config | 5510048 | × | unknown |
| 2692 | config | 5513376 | × | unknown |
| 2688 | config | 5505856 | × | unknown |
| 2688 | config | 5505440 | × | unknown |
| 2592 | config | 5309088 | × | unknown |
| 2602 | | 5329824 | × | unknown |
| 2602 | | 5330592 | × | unknown |
| 2602 | | 5329568 | × | unknown |
| 2602 | | 5330080 | × | unknown |
| 2596 | | 5317536 | × | unknown |
| 2596 | | 5317792 | × | unknown |
| 2596 | | 5318048 | × | unknown |
| 2596 | | 5317280 | × | unknown |
| 2594 | | 5313440 | × | unknown |
| 2594 | | 5312928 | × | unknown |
| 2594 | | 5313184 | × | unknown |
| 2600 | | 5325216 | × | unknown |
| 2598 | | 5321376 | × | unknown |
| 2598 | | 5322144 | × | unknown |
| 2784 | mode location custom config | 5703584 | × | unknown |
| 2784 | mode location custom config | 5703328 | × | unknown |
| 2784 | mode location custom config | 5702816 | × | unknown |
| 2784 | interface network | 5702032 | × | unknown |
| 2784 | interface network | 5702304 | × | unknown |
| 2785 | interface network | 5703808 | × | unknown |
| 2785 | interface network | 5704064 | × | unknown |
| 1757 | interface network | 3600000 | × | unknown |
| 2696 | interface network | 5521552 | × | unknown |
| 2696 | interface network | 5521568 | × | unknown |
| 2720 | | 5570960 | × | unknown |
| 2720 | | 5571232 | × | unknown |
| 2756 | | 5644432 | × | unknown |
| 2756 | | 5644704 | × | unknown |
| 2848 | | 5833104 | × | unknown |
| 2848 | | 5833376 | × | unknown |
| 3104 | | 6357392 | × | unknown |
| 3104 | | 6357664 | × | unknown |
| 2664 | | 5456016 | × | unknown |
| 2664 | | 5456288 | × | unknown |
| 4243 | | 8690064 | × | unknown |
| 4243 | | 8690336 | × | unknown |
| 4243 | | 8689712 | × | unknown |
| 2304 | | 4719008 | × | unknown |
| 2304 | | 4719232 | × | unknown |
| 3106 | | 6361200 | × | unknown |
| 16425 | | 33639248 | × | unknown |
| 48781 | | 99903492 | × | unknown |
| 41609 | | 85215461 | × | unknown |
| 4494 | | 9203775 | × | unknown |
| 25586 | | 52401552 | × | unknown |
| 21214 | | 43446532 | × | unknown |
| 27793 | | 56920439 | × | unknown |
| 26992 | | 55281185 | × | unknown |
| 44308 | | 90744648 | × | unknown |